VMware Horizon VDI on AWS
By Bharath Babbur / Oct 27,2022
Intuitive was approached by a Large Integrated Health Management company to solve a security issue on their current environment which is currently using the normal Remote Desktop Protocol (RDP) to access their business critical application hosted on a Windows platform. This Blog talks about the solution in detail.
Requirement:
The Internal users were accessing critical applications based on SAP BO/DS, and other Windows based agents installed on Normal Windows Boxes enabled with Terminal Services. The Access was primarily via the Remote Desktop Protocol (RDP) on port 3389, which is very commonly used port and liable to security threats and exposure. So, the Customer wanted to put in place a more secure and robust solution, which would not use the normal RDP ports, and thereby solve the potential security issues that may arise.
Limitation and considerations:
- Customer is a VMware shop
- Needs a robust, highly available, simple solution.
- On-Prem SDDC is running on legacy version of vSphere, so latest VDI solution deployment not possible
- Customer has presence on Native AWS
- There are limited users who would be using the VDI Solution (upto a 100 Users) with dedicated desktops
Solution:
Intuitive came up with a solution to deploy VMware Horizon VDI on the Native AWS, using the Windows EC2 instances for the connection servers and the Windows Desktops, without integrating it with the vCenter or using VMware Dynamic Environment Manager (Formerly Known as VMware User Environment Manager) and Unified Access Gateway (UAG)
Logical Design Diagram:
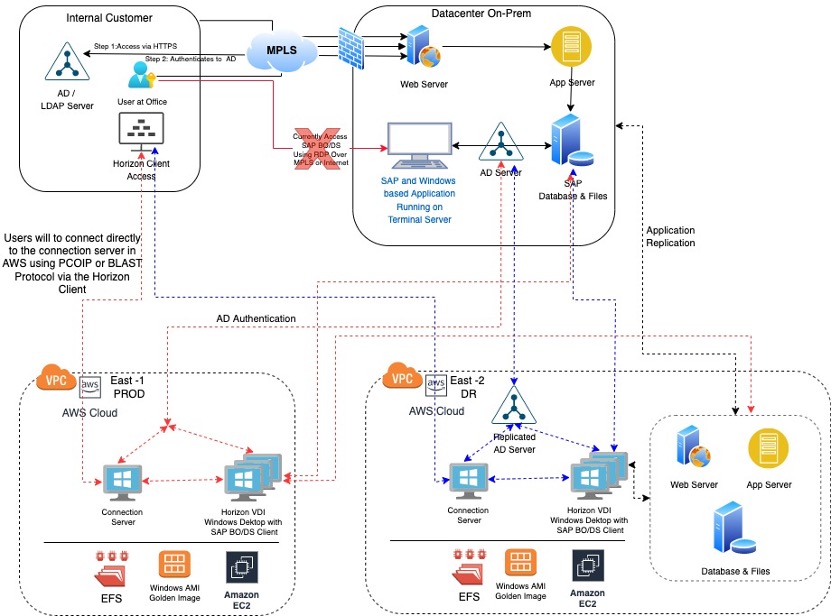
Design Explanation:
Considering the limitation of the vSphere version running on the on-prem site, we decided to use the Native AWS, which would allow us to use and deploy the latest Horizon components versions on the latest Windows OS version as well and ability to take advantages of natively available High Availability built into AWS, additionally we would be closer to the Application in case of a DR as the AWS is the DR Site of the critical applications as well.
Since we cannot deploy any VMware appliances like vCenter and Horizon on the Native AWS, also considering the customer was using dedicated desktops and we do not have the requirement of UAG and DEM along with the integration to vCenter to dynamically create and allocate desktops, we could go into AWS without any issues
We deployed the Prod Horizon component of connection servers in HA Pair with dedicated desktops behind it in the AWS East-1 Prod VPC, which would hair pin back to on-prem Active Directory (AD) service for Authentication and would entitle users to authenticate into the Desktops and connection servers. The users would the use the dedicated desktops streamed using BLAST and PCOIP Protocols to the Horizon clients, which have all the required windows based application \ agents installed on it, which would connect back to the applications and Databases back on-prem. Since the network connectivity between the on-prem site and the AWS VPC was good, we were able to stream the desktops without any major latency issues.
For the DR the on-prem critical application in case of a site down situation would failover to the East-2 DR VPC configured on AWS, so to maintain the locality of the Horizon, we can failover to a similar setup on the East-2 VPC, using a separate connection server URL.




