Network Security and Firewall
By Harsh Viradia / Mar 27, 2023
Network Security faces a wide range of challenges in the modern technology landscape. There are some real-time challenges like evolving threats, advanced persistent threats, insider threats, cloud security.
Threats & Mitigation Techniques
The evolving threat is a major challenge for network security because sophisticated cyber threats are constantly emerging. As the threat evolves, network security professionals must be able to identify and respond to these threats in real-time to protect the network. Threat intelligence and Behavior analyzes techniques can mitigate these challenges. Threat intelligence collects data and analyzes those data from a variety of sources, including security logs, threat feeds, and other security tools so network security professionals can gain a better understanding of the threat and respond to threats effectively. Behavior analysis monitors the traffic and user behavior to identify unusual or suspicious activity. By analyzing all behavior patterns security professionals can identify potential threats and respond to threats so they cannot cause damage to the network.
Advanced Persistent Threats(APTs): Cause & Mitigation
Advanced Persistent Threats(APTs) use advanced techniques to gain access to a network and remain undetected for an extended period. It's difficult to detect and causes significant damage to the network. Intrusion Detection and Prevention Systems (IDPS) monitor whole network traffic and identify potential security threats including APTs. IDPS can identify some known APTs and block them and detect unusual patterns of behavior that may be indicative of an APT. Further, network segmentation divides the network into smaller and secure segments with strict access control and monitoring this will help to limit the impact of an APT and prevent lateral movement across the network.
Cloud Security
The issues associated with cloud computing are enormous for network specialists. Cloud security is a joint obligation between the cloud service provider and the client and entails protecting the network, data, and applications that are housed on the cloud platform. Attackers can now enter systems through virtual computers, containers, and APIs thanks to cloud computing. As a result, the likelihood of an attack on the network surface will rise with more cloud service providers, data centers, and geographic locations. Organizations will find it challenging to obtain visibility into their infrastructure as a result, making it more challenging to spot security issues and take appropriate action. There are numerous products like Cloud Security Broker, which offers visibility and control over cloud apps and data, that may be used to handle all of these concerns. The security posture of cloud infrastructure will be evaluated and managed through cloud security posture management. It will pinpoint vulnerabilities and misconfigurations in their cloud architecture and offer suggestions. IAM controls access to cloud resources and data so that only individuals with authorization can access data. Through employing these technologies, security professionals can more effectively safeguard cloud infrastructure and data. Cloud security generally presents a huge issue for network security.
Firewall:
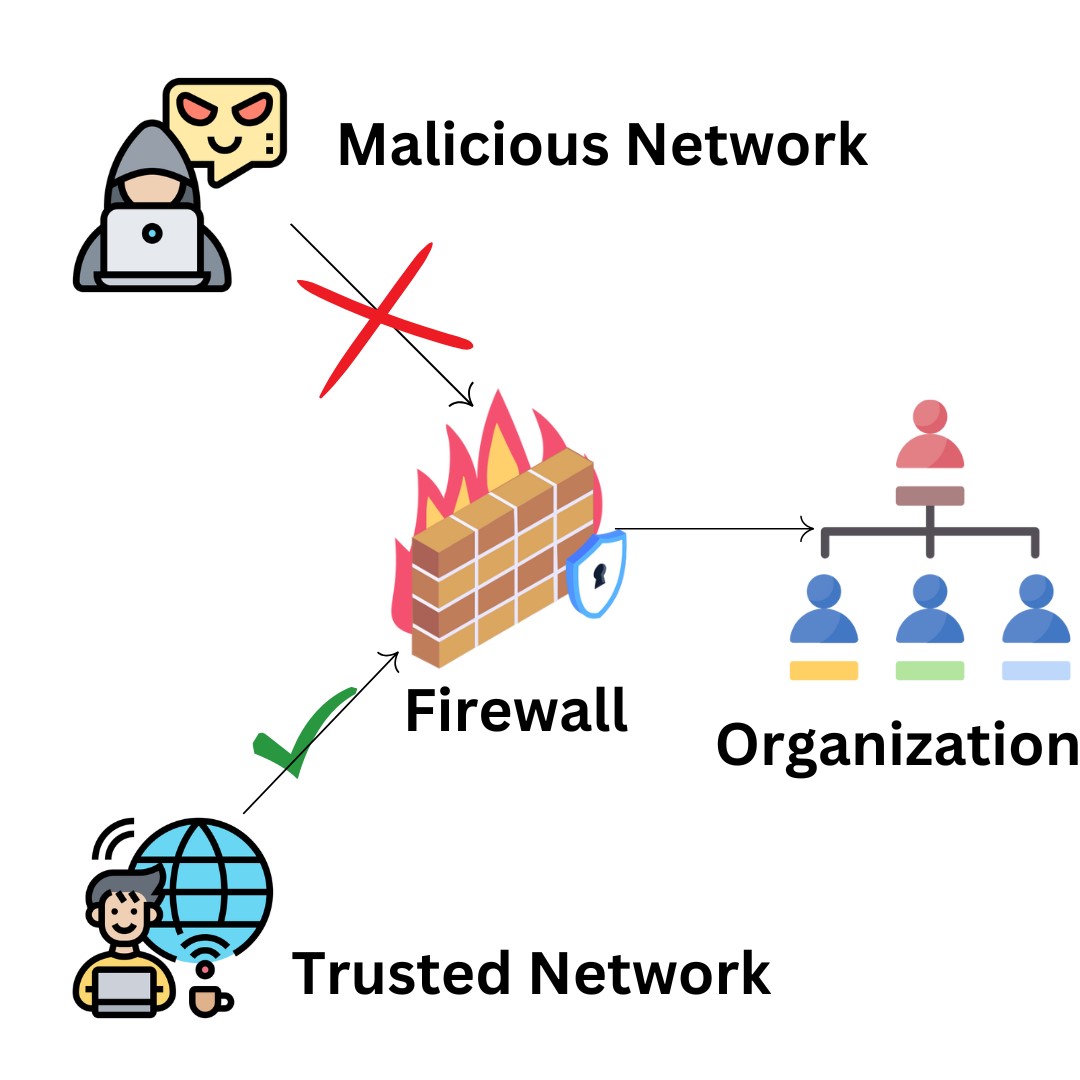
Caption: Working diagram of Firewall
Between a trusted network and an unreliable network, such as the internet, a firewall serves as a barrier. Firewalls, however, encounter several real-time obstacles such improved evasion strategies, encrypted network traffic, scalability, application-level assault, etc. due to the continually growing danger and rising sophistication of attacks.
Attackers always develop new threats and strategies to get around firewalls and exploit security holes to access networks. For instance, the firewall may include a rule to stop some known malware or viruses, but it's possible that it won't stop a zero-day exploit or that a new type of malware isn't mentioned in the rule, making it impossible to recognize it as a danger. Attackers attempt to enter a network by focusing on these gaps. Distributed networks enhance the attack surface for possible threats since users can access the network from many locations. Because of this, firewall monitoring of network traffic is challenging. Modern firewalls, intrusion detection and prevention systems (IDPS), threat intelligence, and machine learning will all enable the firewall stay current with the newest danger and give protection against both new and old attacks to solve these difficulties.
Advanced Evasion Techniques (AETs)
Hackers deploy Advanced Evasion Techniques (AETs) to circumvent the network. AETs functioned by exploiting flaws in network protocols, allowing attackers to deliver malicious communications. This is how attackers get through the firewall and into the network. There are several approaches to this problem, such as sandboxing, dots per inch, and so on. Sandboxing is a method of preventing AETs. Sandboxing is the process of running potentially harmful code in a virtual environment to analyze behavior and detect malicious behavior. For example, this firewall detects AETs that may circumvent typical security procedures. DPI scans each packet of network traffic, payload, and header information to identify risks. A firewall can detect AETs that are masquerading as genuine traffic at this level of examination.
Encrypted traffic
Encrypted traffic presents a challenging issue for network firewalls since encryption adds an extra degree of security and is sometimes used by attackers to conceal unwanted behavior. One of the most difficult aspects of encrypting communication is that no one can see what the traffic includes in plain text. As a result, existing firewall technologies such as IDPS and intrusion detection may be unable to detect threats hidden within encrypted data. Secure Sockets Layer (SSL)/Transport Layer Security (TLS) decryption is one method for analyzing encrypted traffic. This entails intercepting encrypted traffic and decrypting it in real time in order to assess traffic content. This firewall's machine learning algorithms and behavior analysis can detect possible threats without decrypting the communication.
Scalability
Scalability is a major difficulty for network firewalls, particularly in large enterprises with significant network traffic volumes. When traffic volume increases, the firewall must be able to scale without compromising performance or security. The typical firewall may be incapable of handling high volumes of traffic. Firewalls can become overburdened, resulting in decreased performance, increased latency, and even downtime. In this case, distributed traffic can be beneficial. Several firewalls in different places will lessen network traffic stress. For scalability and flexibility, the second alternative is a cloud-based firewall. Because a firewall is a virtual instance in the cloud, it can be quickly scaled up and down without the need for extra hardware.
Application-level attacks
Network firewalls face significant challenges from application-level attacks. SQL injection, cross-site scripting, and buffer overflow attacks are examples of application-level attacks. These attacks are difficult to detect for network firewalls because they frequently exploit unique weaknesses in individual programs or application protocols. One technique to analyzing and inspecting application-level traffic and preventing application-level assaults is to use modern firewalls. DEEP PACKET INSPECTION (DPI) is another method for inspecting application-level communication in real time. This method examines each packet of communication, identifying application protocols and detecting threats or irregularities. One method for preventing application-level attacks is to use an application firewall. Application-level firewalls prevent application-level attacks by combining signature-based detection, behavior analysis, and traffic shaping.
Conclusion
All these strategies are useful for preventing attackers from gaining network access, but attackers are constantly creating new techniques, therefore firewalls must evolve to stay up with the latest danger and provide effective network protection.




